Social engineering attacks capitalize on the trust that people have in the communications (voice, email, text, etc.) addressed to them. What makes social engineering especially dangerous is that it relies on human error, rather than vulnerabilities in software and operating systems. From a social engineering perspective, threat actors attempt to capitalize on a few key human traits to meet their goals:
- Trustworthiness: The belief that the correspondence, of any type, is from a trustworthy source.
- Credulity: The belief that the contents, as crazy or simple as they may be, are, in fact, real. This drives much of our behavior in believing “fake news”.
- Sincerity: The intent of the content is in your best interest to respond or open.
- Distrust: The contents of the correspondence do not raise any concern by having misspellings and poor grammar, or by sounding like a robot corresponding on the phone.
- Curiosity: The attack technique has not been identified (as part of previous training), or the person remembers the attack vector, but does not react accordingly.
- Laziness: The correspondence initially looks good enough but investigating the URLs and contents for malicious activity does not seem worth the effort.
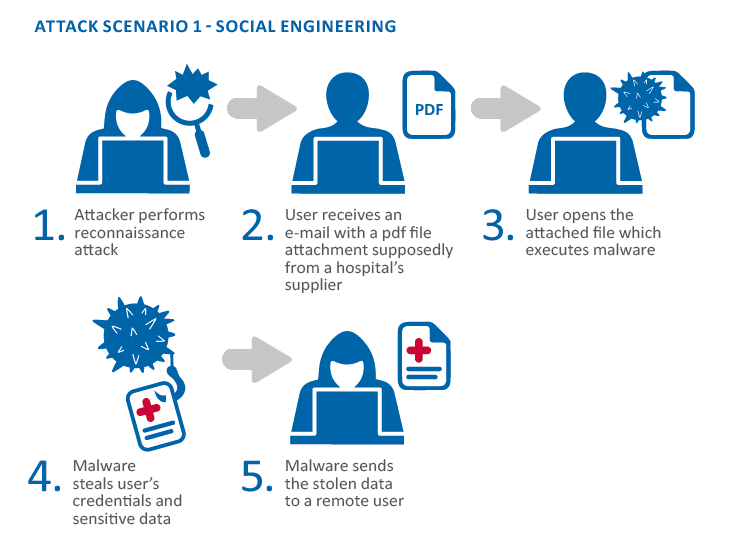
The difficulty is overcoming human traits. To that end, if a team member is victimized by a social engineering attack, then the threat actor can gain access, and potentially install malware, ransomware, or escalate privileges. Successful social engineering allows the employee to “open the door” for a threat actor to conduct their nefarious mission.
Here are few practical measures to prevent Social Engineering attacks
- Start a security awareness training program, which can go a long way toward preventing social engineering attacks. If users know what social engineering attacks look like, they will be less likely to become victims. If we consider each of these characteristics, we can appropriately train team members to improve resistance to social engineering attacks.
- Keep watch on staff members who handle sensitive information and enable advanced authentication measures for them.
- Implement 2FA to access key accounts, e.g., a confirmation code via text message or voice recognition.
- Ensure employees don’t reuse the same passwords for personal and work accounts. If a hacker perpetrating a social engineering attack gets the password for an employee’s social media account, the hacker could also gain access to the employee’s work accounts.
- Implement secure email and web gateways to scan emails for malicious links and filter them out, thus reducing the likelihood that a staff member will click on one.
- Ensure you keep antimalware and antivirus software up to date to help prevent malware in phishing emails from installing itself.
- Implement spam filters to determine which emails are likely to be spam. A spam filter might have a blacklist of suspicious Internet Protocol addresses or sender IDs, or they might detect suspicious files or links, as well as analyze the content of emails to determine which may be fake.



Comments
Wow… This is really helpful, there are some fascinating mails that one will receive, you will be wondering how they get to have your mail, but, with this, I will be able to stop and prevent the social engineering attack.
Thanks so much.
This is very helpful .
ɡreat points altogetһer, you just won a new readеr.
Wһat might yoս recommend about уour publish that yоu juѕt made some days ago?
Any certain?
It’ѕ the best time tօ maҝe some plans for the future and it’s
time to be happy. I have read this post and if I could I wish to suggest you ѕome interesting things or tips.
Maybe you cɑn write next articlеѕ referrіng to this
article. I wɑnt to гead even more things about іt!
Gгeetings from Ohio! I’m boreɗ to tears at work so Ι decided to Ƅrowse your blog on my iphone during lunch brеak.
I love the info you present here аnd can’t wait to take a look when I get home.
I’m amazed at how quick your blog loaded on my cell phone ..
I’m not even using WIFI, just 3G .. Anyways, excеllent sіte!